Transforming medical equipment procurement globally

Why Cybersecurity Medical Devices Matter More Than Ever
Cybersecurity medical devices are critical because they protect patient safety, healthcare operations, and sensitive health data in an increasingly connected world. Here's what you need to know:
Key Facts About Medical Device Cybersecurity:
- 94% of healthcare organizations have been victims of cyberattacks
- Connected devices create vulnerabilities that can directly harm patients
- Cyberattacks worldwide are expected to double by 2025
- Compromised devices can disrupt entire hospital networks and delay critical care
- Regulatory bodies worldwide now mandate cybersecurity measures throughout device lifecycles
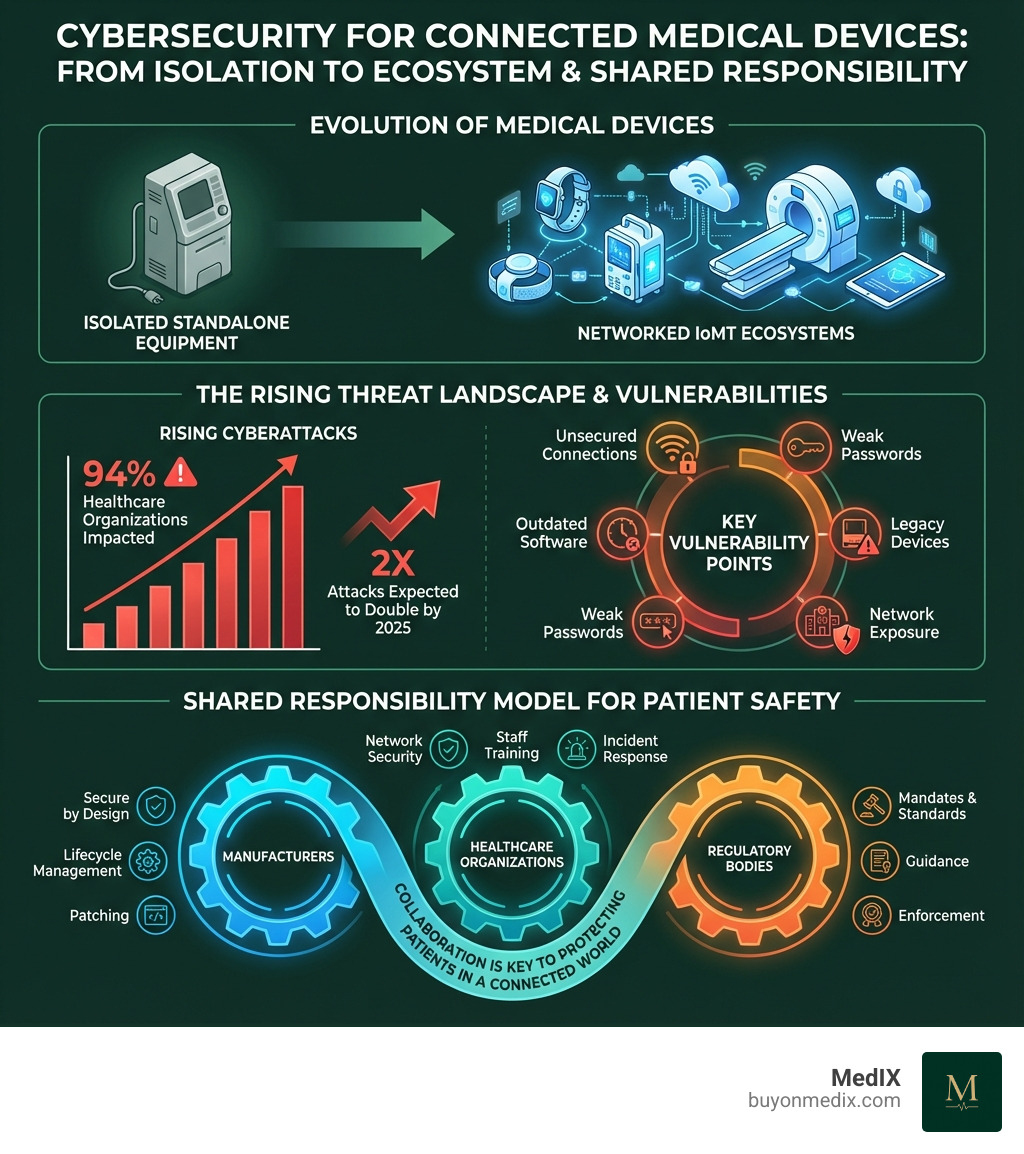
Medical devices have evolved dramatically. What were once standalone, isolated pieces of equipment are now networked systems that exchange vital patient information across hospital networks, connect to the internet, and communicate with mobile devices. This connectivity brings tremendous benefits for patient care—but it also exposes devices to the same cyber threats that target other computer systems.
The stakes are incredibly high. A compromised infusion pump could deliver incorrect medication dosages. A hacked pacemaker could be manipulated remotely. Ransomware can lock entire hospital systems, forcing emergency rooms to turn away patients. As one academic study noted, "the increased connectivity to existing computer networks has exposed medical devices to cybersecurity vulnerabilities from which they were previously shielded."
For procurement managers in healthcare institutions, this creates a new challenge. Beyond traditional concerns like quality, pricing, and regulatory compliance, you now need to evaluate the cybersecurity posture of every connected device you purchase. The decision you make today about a medical device's security features could directly impact patient safety tomorrow.
The good news? Regulatory frameworks, industry standards, and best practices are evolving to address these risks. Understanding cybersecurity for medical devices isn't just about IT—it's about protecting patients in a connected world.
The Expanding Threat Landscape and Its Impact on Patient Safety
The digital change in healthcare has brought incredible advancements but also a new era of risk. Medical devices, once isolated, are now intertwined with hospital networks and the internet, creating an expansive attack surface. This makes cybersecurity medical devices a direct matter of patient safety and healthcare continuity, not just an IT concern.

The statistics are stark: 94% of healthcare organizations have suffered a cyberattack, leading to potential patient harm and service disruptions. With cyberattacks expected to double by 2025, both medical device manufacturers and health delivery organizations (HDOs) face unprecedented pressure to be vigilant.
Key threats to cybersecurity medical devices
Threats to medical devices are diverse and evolving. Cyber actors target healthcare for its valuable data, reliance on electronic health records (EHRs), and perceived security weaknesses. As the FBI has warned, these cyber intrusions are likely to increase.
Some of the primary threats include:
- Ransomware: Locks down systems and data, demanding payment. In hospitals, it can halt operations, force patient diversions, and severely impact care.
- Malware: Includes viruses, worms, and spyware designed to disrupt device function, steal data, or gain unauthorized access, as seen in attacks on VA medical devices.
- Phishing: Uses social engineering to trick staff into revealing sensitive information or clicking malicious links, compromising network or device control.
- Denial-of-Service (DoS) attacks: Flood a system with traffic, making critical monitoring or life-sustaining equipment unresponsive.
- Unauthorized Access: Gaining control over a device by exploiting weak passwords, unpatched vulnerabilities, or insecure networks. Common vulnerabilities include unsecured web interfaces and default passwords.
These threats are no longer theoretical; they are a clear and present danger to our healthcare infrastructure.
How IoMT Increases Cybersecurity Challenges
The Internet of Medical Things (IoMT) connects everything from pacemakers to imaging systems, enabling real-time monitoring and remote care. However, this connectivity also expands the attack surface. Each connection point—to an EHR, patient app, or cloud server—is a potential vulnerability. Interoperability, while crucial for efficiency, means a compromise in one device can spread to others. Therefore, assessing the entire ecosystem's security, not just individual devices, is essential.
The Real-World Impact on Patients and Hospitals
Vulnerabilities in cybersecurity medical devices have dire consequences for patient safety and hospital operations. Real-world scenarios include:
- Compromised infusion pumps: Attackers could alter medication dosages, directly endangering patient lives.
- Altered pacemaker settings: Manipulation of implantable device settings could have fatal outcomes.
- Inaccurate diagnostic imaging: Compromised MRIs or CTs can lead to misdiagnosis and delayed treatment.
- Stolen Protected Health Information (PHI): Breaches of sensitive patient data can lead to identity theft and fraud. The number of individuals impacted by healthcare hacks grew from 27 million in 2020 to 74 million in 2023.
- Delayed or canceled procedures: Ransomware can render equipment unusable, forcing delays in critical surgeries and procedures.
These examples underscore why patient safety is the paramount concern when adopting connected technology.
Navigating the Global Regulatory Maze for Cybersecurity Medical Devices
Securing medical devices is a shared responsibility, with regulatory bodies worldwide mandating robust security measures across the product lifecycle. For manufacturers and providers, complying with these frameworks is essential for market access, avoiding penalties, and safeguarding patient safety.

Key Regulatory Frameworks and Standards
The global landscape for cybersecurity medical devices is shaped by regulations and standards designed to protect patients and data. International harmonization efforts are underway, led by groups like the International Medical Device Regulators Forum (IMDRF).
Here are some of the most influential frameworks:
- US Food and Drug Administration (FDA): The FDA is central to addressing cybersecurity risks, issuing guidance for premarket and postmarket management.
- PATCH Act: This 2023 law amended the FD&C Act, adding section 524B to mandate stringent cybersecurity requirements across the device lifecycle. Manufacturers of "cyber devices" must now submit detailed cybersecurity information in premarket submissions.
- Premarket Submission Requirements: The FDA requires cybersecurity details in all premarket submissions (510(k), PMA, De Novo). As of October 1, 2023, electronic submissions via eSTAR that lack this information will be put on hold.
- European Union Medical Device Regulation (EU MDR) and In Vitro Diagnostic Regulation (EU IVDR): These regulations make cybersecurity a critical component of device safety and performance for EU market access.
- ISO 14971 (Medical devices – Application of risk management to medical devices): Provides a systematic approach to risk management, crucial for integrating cybersecurity risks into the overall assessment process.
- IEC 62304 (Medical device software – Software life cycle processes): Outlines processes for the safe design and maintenance of medical device software, integrating security measures during development.
- IEC 81001-5-1 (Health software and health IT systems safety, effectiveness and security – Part 5-1: Security – Activities in the product lifecycle): Extends risk management principles specifically to cybersecurity for health software and IT systems.
- ISO/IEC 27001 (Information security management systems – Requirements): A global standard for an information security management system (ISMS) to ensure data confidentiality, integrity, and availability, supporting compliance with GDPR and other regulations.
Guidance from bodies like Health Canada also requires manufacturers to incorporate cybersecurity into their risk management processes.
Data Privacy Implications: HIPAA, GDPR, and Beyond
The sensitive nature of patient health information (PHI) makes data privacy a paramount concern. Regulations like HIPAA and GDPR impose strict requirements on data handling.
- HIPAA (Health Insurance Portability and Accountability Act): The HIPAA Security Rule requires healthcare organizations (HDOs) to implement safeguards like encryption, access controls, and software updates to protect electronic PHI (ePHI) on medical devices.
- GDPR (General Data Protection Regulation): In the EU, GDPR sets stringent standards for data protection, requiring clear consent for data processing and robust security to prevent breaches, with significant fines for non-compliance.
Globally, other regulatory bodies also enforce data privacy:
- Therapeutic Goods Administration (Australia)
- Brazilian Health Regulatory Agency (ANVISA) (Brazil)
- Health Canada
- National Medical Products Administration (China)
- European Commission - Directorate-General for Health and Food Safety (EU)
- Pharmaceutical and Medical Devices Agency (PMDA) (Japan)
- Medicines and Healthcare products Regulatory Agency (UK)
- Swissmedic (Switzerland)
- World Health Organization (WHO) (Global guidance)
These regulations emphasize the need for privacy-by-design principles and secure configurations.
The Role of a Software Bill of Materials (SBOM)
A Software Bill of Materials (SBOM) is a cornerstone of medical device cybersecurity, acting as an "ingredient list" for all software components.
An SBOM contributes to cybersecurity by:
- Transparency: Providing a clear view of a device's software composition to identify potential vulnerabilities.
- Vulnerability Management: Allowing quick identification of affected devices when a vulnerability is disclosed. MITRE offers guidance on SBOM processing challenges.
- FDA Requirements: The FDA and Health Canada now require an SBOM (or CBOM) for certain device submissions to help manage risks.
- Component Tracking: Facilitating tracking of software components for more efficient patching and updates.
SBOMs empower stakeholders to better manage cybersecurity risks in software-driven medical devices.
A Lifecycle Approach to Medical Device Security
Effective cybersecurity medical devices requires a continuous process spanning the entire product lifecycle, from design to decommissioning. This lifecycle approach is essential for building resilience against evolving threats and ensuring patient safety.
Responsibilities of Medical Device Manufacturers
Manufacturers are responsible for embedding cybersecurity throughout the product lifecycle, starting from the design phase.
Key responsibilities include:
- Secure Product Development Framework (SPDF): Establishing processes to reduce vulnerabilities throughout the device lifecycle, integrated with risk management and quality systems.
- Secure Design and Threat Modeling: Building security into the design from the start and using threat modeling to proactively identify attack vectors.
- Cybersecurity Risk Assessment: Conducting assessments focused on exploitability for all software components, in parallel with safety risk management.
- Software Bill of Materials (SBOM): Generating and maintaining an SBOM for transparency and vulnerability management.
- Cybersecurity Testing: Performing robust testing, including vulnerability scanning and penetration testing, to verify security controls.
- Coordinated Vulnerability Disclosure (CVD): Establishing processes to receive, assess, and responsibly disclose vulnerabilities and mitigations.
- Post-market Surveillance and Updates: Continuously monitoring for new threats and providing timely software patches and updates throughout the device's service life.
The FDA's guidance on "Quality System Considerations and Content of Premarket Submissions" helps manufacturers meet these obligations.
How Healthcare Organizations Can Implement Solutions
Healthcare organizations (HDOs) are on the front lines and must implement solutions to protect patients and ensure operational continuity.
Effective strategies include:
- Comprehensive Asset Inventory: Maintain an accurate inventory of all medical devices, their software versions, and network configurations.
- Secure Network Configuration: Use network segmentation to isolate medical devices, especially critical care equipment, to limit the spread of threats.
- Continuous Monitoring: Monitor network traffic and device behavior to detect unusual activity or potential attacks in real-time.
- Incident Response Planning: Develop and test a robust incident response plan for medical device security incidents. MITRE's incident response playbook is a valuable resource.
- Staff Training and Awareness: Regularly train all staff on cybersecurity best practices. The FDA provides resources like Cybersecurity Awareness for Connected Medical Devices.
- Collaboration with Manufacturers: Work with manufacturers to understand security features, receive updates, and coordinate on vulnerabilities.
- Risk Management Integration: Integrate medical device cybersecurity into the organization's broader risk management framework.
Best practices for securing legacy cybersecurity medical devices
Legacy devices, which may run outdated software but remain critical to care, pose a unique challenge. Securing them requires pragmatic approaches.
- Identify and Assess: Conduct a risk assessment of all legacy devices to understand their vulnerabilities.
- Network Segmentation: Isolate legacy devices on segmented networks, ideally without internet access, to limit their exposure.
- Compensating Controls: When patching isn't possible, use alternative measures like virtual patching (using firewalls to block exploits), strong access controls, and continuous monitoring.
- Documentation and Procedures: Develop clear operational procedures for using and maintaining these devices securely.
- End-of-Life Planning: Create a plan to phase out and replace devices that cannot be adequately secured.
- Collaboration: Work with manufacturers or third-party experts for support and guidance.
- IMDRF Guidance: Follow recommendations from bodies like the IMDRF and resources like MITRE's report on managing legacy device risks.
The goal is to extend the secure life of these devices while minimizing patient risk.
Frequently Asked Questions about Medical Device Cybersecurity
Navigating the complexities of cybersecurity medical devices can raise many questions. Here, we address some of the most common inquiries to provide clarity and guidance.
What is the biggest cybersecurity risk for medical devices?
The biggest risks fall into two categories with severe patient safety implications. The first is unauthorized manipulation of a device's function, such as an attacker altering an infusion pump's dosage, which could directly cause patient harm or death. The second is large-scale disruption of healthcare services via ransomware, which can render hospital networks and devices inoperable, leading to canceled procedures and operational chaos. The interconnectedness of IoMT and the value of healthcare data amplify these threats.
Who is responsible for securing a medical device?
Security is a shared responsibility model involving multiple stakeholders:
- Medical Device Manufacturers must build secure devices ("security by design"), conduct risk assessments, provide regular software patches, and manage vulnerability disclosures.
- Healthcare Delivery Organizations (HDOs) must securely configure and maintain devices on their networks. This includes network segmentation, access controls, continuous monitoring, and staff training.
- Patients and Clinicians play a role by following security best practices, such as using strong passwords and reporting suspicious device behavior.
While manufacturers build the foundation, HDOs must actively manage the security of their device ecosystem.
How does the FDA regulate medical device cybersecurity?
The FDA regulates cybersecurity medical devices by addressing risks throughout the entire lifecycle.
- Premarket Requirements: The FDA, through regulations like the PATCH Act, mandates that manufacturers submit detailed cybersecurity information, including an SBOM, in premarket submissions (e.g., 510(k), PMA) to demonstrate robust security controls.
- Post-market Monitoring and Management: The FDA requires manufacturers to have processes for monitoring and addressing post-market vulnerabilities, including providing timely security patches. The agency issues guidance and safety alerts to inform the healthcare community.
- Quality System Regulation: Cybersecurity is an integral part of a device's safety and effectiveness under the FDA's Quality System Regulation, requiring manufacturers to adhere to cybersecurity requirements within their quality systems.
The FDA's framework evolves to meet new threats with a proactive, risk-based approach.
Conclusion
The landscape of cybersecurity medical devices is complex and constantly changing, but our commitment to patient safety remains unwavering. As medical devices become more interconnected, the need for robust cybersecurity strategies has escalated from a technical concern to a fundamental aspect of healthcare delivery and trust.
We've seen that the threats are real and growing, with cyberattacks on healthcare organizations becoming alarmingly common. The integration of devices into the Internet of Medical Things (IoMT) brings incredible benefits but also expands the attack surface, making every connected device a potential point of vulnerability. The direct impact on patient safety, from manipulated dosages to compromised personal health information, underscores the critical importance of our collective efforts.
Fortunately, a robust framework of regulatory standards and best practices is emerging globally. From the FDA's stringent premarket and postmarket requirements, including the critical PATCH Act and the use of SBOMs, to international standards like ISO 14971 and IEC 81001-5-1, the industry is moving towards a more secure future. Data privacy regulations like HIPAA and GDPR further reinforce the necessity of protecting sensitive patient data.
Safeguarding cybersecurity medical devices requires a shared responsibility model. Manufacturers must embed security throughout the entire product lifecycle, from secure design and threat modeling to continuous post-market surveillance and timely updates. Healthcare organizations, in turn, must implement secure network configurations, rigorous asset management, continuous monitoring, and comprehensive incident response plans. Even for legacy devices, creative solutions like network segmentation and compensating controls can significantly mitigate risks.
At MedIX, we understand the critical importance of secure medical equipment. We're dedicated to connecting hospitals and clinics with certified medical equipment suppliers who prioritize these cybersecurity standards. Through AI-matching, rigorous compliance checks, and reliable global logistics, we ensure that the verified equipment you procure not only meets your clinical needs but also improves the cybersecurity posture of your institution.
Continuous vigilance, proactive strategies, and unwavering collaboration between manufacturers, healthcare providers, and regulators will be essential. By embracing a comprehensive approach to cybersecurity medical devices, we can collectively protect patients and ensure the integrity of healthcare in our increasingly connected world.
Explore verified medical equipment through MedIX today.
Expert voices
Insights from leaders transforming medical equipment procurement






More from our blog
Discover the latest trends in medical technology and procurement
Stay ahead of medical technology
Get the latest insights, research, and market updates delivered straight to your inbox
Ready to transform your procurement
Discover how MedIX can streamline your medical equipment sourcing process



